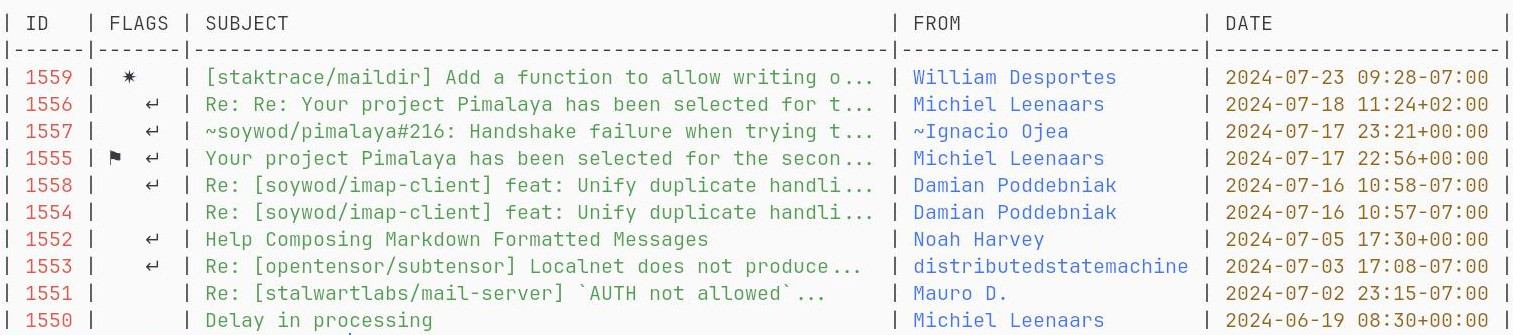
```
$ himalaya envelope list --account posteo --folder Archives.FOSS --page 2
```
## Features
- Multi-accounting
- Interactive configuration via **wizard** (requires `wizard` feature)
- Mailbox/folder management (**create**, **list**, **expunge**, **purge**, **delete**)
- Envelope **listing**, **filtering** and **sorting**
- Message composition based on `$EDITOR`
- Message manipulation (**copy**, **move**, **delete**)
- Basic backends:
- **IMAP** (requires `imap` feature)
- **Maildir** (requires `maildir` feature)
- **Notmuch** (requires `notmuch` feature)
- Default backends:
- **SMTP** (requires `smtp` feature)
- **Sendmail** (requires `sendmail` feature)
- PGP encryption:
- via shell commands (requires `pgp-commands` feature)
- via [GPG](https://www.gnupg.org/) bindings (requires `pgp-gpg` feature)
- via native implementation (requires `pgp-native` feature)
- Global system **keyring** for managing secrets (requires `keyring` feature)
- **OAuth 2.0** authorization (requires `oauth2` feature)
- **JSON** output via `--output json`
*Himalaya CLI is written in [Rust](https://www.rust-lang.org/), and relies on [cargo features](https://doc.rust-lang.org/cargo/reference/features.html) to enable or disable functionalities. Default features can be found in the `features` section of the [`Cargo.toml`](https://github.com/pimalaya/himalaya/blob/master/Cargo.toml#L18).*
## Installation
Himalaya CLI can be installed with a prebuilt binary:
```bash
# As root:
$ curl -sSL https://raw.githubusercontent.com/pimalaya/himalaya/master/install.sh | sudo sh
# As a regular user:
$ curl -sSL https://raw.githubusercontent.com/pimalaya/himalaya/master/install.sh | PREFIX=~/.local sh
```
These commands install the latest binary from the GitHub [releases](https://github.com/pimalaya/himalaya/releases) section.
*Binaries are built with [default](https://github.com/pimalaya/himalaya/blob/master/Cargo.toml#L18) cargo features. If you want to enable or disable a feature, please use another installation method.*